Did you know how much stuff you can do with an ip address?
There is a plenty of tutorials that go into how to get an IP Address from the preferred mark of your choice. Now I will not go into that subject. Alright so say we got the targets IP Address finally. What do we do with this IP Address. Well first you should ping the IP Address to make sure that its alive or how we say online. Now at the bottom I will include some links where you can get some key tools that may help on your journey through the electronic jungle. So we need to find places to get inside of the computer so we can start trying to find a way to "hack" that. Port Scanners are used to identify the open ports on a machine thats running on a network, whether its a router, or a desktop computer, they all have ports. Protocols use these ports to communicate with other services and resources on the network. Well Blues Port Scanner will scan the IP address that you chose and identify open ports that are on the target box.
Blues Port Scaner you can download from here:
For example:
Idlescan using Zombie <Domain Name> (192.150.13.111:80); Class: Incremental
Interesting ports on 208.225.90.120:
(The 65522 ports scanned but not shown below are in state: closed)
Port State Service
21/tcp open ftp
25/tcp open smtp
80/tcp open http
111/tcp open sunrpc
135/tcp open loc-srv
443/tcp open https 1027/tcp open IIS
1030/tcp open iad1
2306/tcp open unknown
5631/tcp open pcanywheredata
7937/tcp open unknown
7938/tcp open unknown
36890/tcp open unknown
In example we see that there are a variety of ports open on this box. Take note of all the ports that you see listed before you. Most of them will be paired up with the type of protocol that uses that port (IE. 80-HTTP 25-SMTP Etc.). Take all that information and paste it into notepad or the editor of your choice. This is the beginning of your targets record. So now we know what ports are open. These are all theoretical points of entry where we could wiggle into the computer system. But we all know its not that easy. Alright so we dont even know what type of software or what operating system that this system is running.
NMAP the Port Scanner has unique OS fingerprinting methods so when the program sees a certain series of ports open it uses its best judgement to guess what operating system its running.
NMAP you can download here:
So we have to figure out what type of software this box is running if we are gonna start hacking the thing right? Many of you have used TELNET for your MUDS and MOOS and weird multiplayer text dungeons and many of you havent even heard of it before period. TELNET is used to open a remote connection to an IP Address through a Port. So this means is we are accessing their computer from across the internet, all we need is their IP address and a port number. With that record you are starting to compile, open a TELNET connection to the IP Address and enter one of the open ports that you found on the target.
So say we typed 'TELNET -o xxx.xxx.xxx.xxx 25' This command will open up a connection through port 25 to the IP xxx.xxx.xxx.xxx. Now you may see some text at the very top of the screen. You may think how is text going to help me. Well It will. Get that list you are starting to write, and copy the banners into your compilation of the information youve gathered on your target. Banners/Headers are what you get when you TELNET to the open ports. Heres an example of a banner from port 25.
220 jesus.gha.chartermi.net ESMTP Sendmail 8.12.8/8.12.8; Fri, 7 Oct 2005 01:22:29 -0400
Now this is a very important part in the enumeration process. You notice it says 'Sendmail 8.12.8/8.12.8' Well what do you know, we now have discovered a version number. This is where we can start identifying the programs running on the machine. There are some instances in which companies will try and falsify their headers/banners so hackers are unable to find out what programs are truly installed. Now just copy all the banners from all the open ports *Some Ports May Have No Bannners* and organize them in the little record we have of the target. Now we have all the open ports, and a list of the programs running and their version numbers. This is some of the most sensitive information you can come across in the networking world. Other points of interest may be the DNS server, that contains lots of information and if you are able to manipulate it than you can pretend to hotmail, and steal a bunch of peoples email. Well now back to the task. Apart from actual company secrets and secret configurations of the network hardware, you got some good juicy info.
http://www.securityfocus.com is a very good resource for looking up software vulnerabilities. If you cant find any vulnerabilities there, search on google. There are many, many, many other sites that post vulnerabilities that their groups find and their affiliates.
At SecurityFocus you can search through vendor and whatnot to try and find your peice of software, or you can use the search box. When i searched SecurityFocus i found a paper on how Sendmail 8.12.8 had a buffer overflow. There was proof of concept code where they wrote the shellcode and everything, so if you ran the code with the right syntax, a command prompt would just spawn. You should notice a (#) on the line where your code is being typed. That pound symbol means that the command prompt window thats currently open was opened as root. The highest privilage on a UNIX/Linux Box. You have just successfully hacked a box. Now that you have a command shell in front of you, you can start doing whatever you want, delete everything if you want to be a jerk, however that is not recommended. Maybe leave a text file saying how you did it and that they should patch their system. Whoever they are. And many times the best thing you can do is just lay in the shadows, dont let anyone know what you did. More often than not this is the path you are going to want to take to avoid unwanted visits by the authorities.
There are many types of exploits out there, some are Denial of Service exploits, where you shut down a box, or render an application/process unusable. Called denial of service simply because you are denying a service on someones box to everyone trying to access it. Buffer Overflow exploits are involved when a variable inside some code doesnt have any input validation. Each letter you enter in for the string variable will be 1 byte long. Now where the variables are located at when they are in use by a program is called the buffer. Now what do you think overflowing the buffer means. We overflow the buffer so we can get to a totally different memory address. Then people write whats called shellcode in hex. This shellcode is what returns that command prompt when you run the exploit. That wasnt the best description of a buffer overflow, however all you need to remember is that garbage data fills up the data registers so then the buffer overflows and allows for remote execution of almost every command available. There are many, many other types of attacks that cannot all be described here, like man-in-the-middle attacks where you spoof who you are. Performed correctly, the slave will enter
http://www.bank.com and his connection will be redirected to your site where you can make a username and password box, make the site look legit. And your poor mark will enter their credentials into your site, when they think its really
http://www.bank.com. You need to have a small script set up so it will automatiically display like an error or something once they try and log in with their credentials. This makes it seem like the site is down and the slave doenst give it a second thought and will simply try again later.
So as a summary of how to own a box when you only have an IP Address
Method Works On both *Nix and Windoze
You can do the same with domain names (IE google.com) than what you can with IP Addresses. Run a whois Lookup or something along those lines. Or check up on InterNIC you should be able to resolve the domain name to an IP address.
- Port Scan The Address And Record Open Ports
- Telnet To Open Ports To Identify Software Running On Ports
netcat - Network swiss army knife. Like TELNET only better and with a lot more functionality. Both can be used when you are trying to fingerprint software on open ports
- Record Banners And Take Note Of The Application Running and The Version Number
- Take A Gander Online At SecurityFocus.com or Eeye.com. If you cant find any vulnerabilities then search google.
- Make a copy of some Proof-Of-Concept code for the vulnerability.
I will not teach you how to cover your track. This is prohibited and i put that here only for informational reasons.




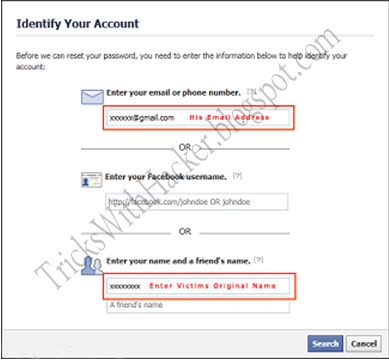
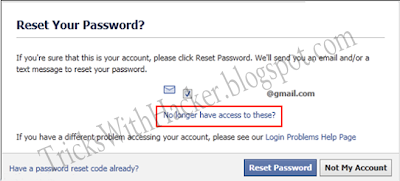
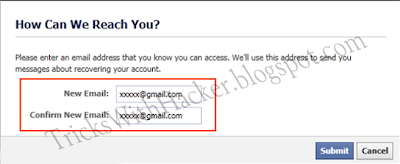
 There are various methods to hack facbook account password like Keyloggers, Phishing websites etc.. whereas bruteforcing, dictionary attacks, DDOS attack etc will not work directly due account lockout feature. Today in this post I am going to share a very effective way to hack facebook account I named it Hacking with Trusted Friends.
There are various methods to hack facbook account password like Keyloggers, Phishing websites etc.. whereas bruteforcing, dictionary attacks, DDOS attack etc will not work directly due account lockout feature. Today in this post I am going to share a very effective way to hack facebook account I named it Hacking with Trusted Friends.